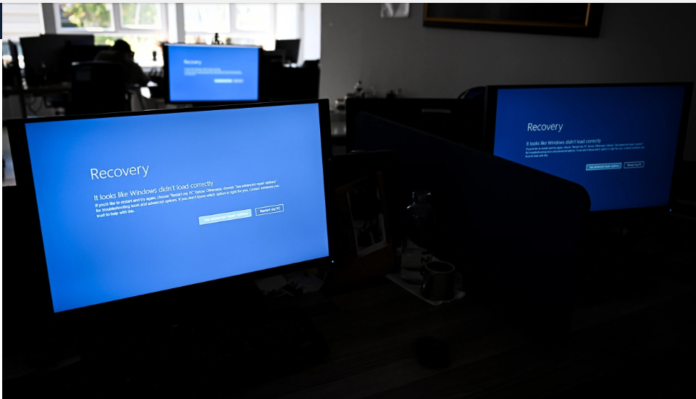
How the flawed code entered the upgrade and why it wasn’t found prior to its public distribution are mysteries.

SAN FRANCISCO: Security experts claim that CrowdStrike’s usual upgrade of its popular cybersecurity software seems not to have undergone sufficient quality checks before to deployment, as seen by the worldwide computer system crashes triggered by the malware on Friday.
By upgrading the threats it fights against, the most recent version of Falcon Sensor software was designed to increase the security of CrowdStrike customers’ systems against hacking. However, one of the most extensive tech outages in recent memory for businesses using Microsoft’s Windows operating system was caused by flawed code in the update files.

There was disruption in international banking, airlines, hospitals, and government agencies. CrowdStrike provided instructions on how to repair the impacted systems, but specialists predicted that it would take some time to bring them back up since the faulty code needed to be manually removed.
“What it appears to be is that this file may have escaped detection during the vetting or sandboxing process that they use to examine code,” said Steve Cobb, chief security officer at Security Scorecard, whose systems were also affected by the problem.
After the upgrade was released on Friday, issues were apparent very immediately. Users shared images of PCs with blue screens showing error warnings on social media. In the business, they are referred to as “blue screens of death.”
Security researcher Patrick Wardle, who focuses on researching risks against operating systems, claimed his examination located the malware causing the outage.
According to him, the issue with the upgrade occurred “in a file that contains either configuration information or signatures.” These signatures are pieces of code that identify certain kinds of malware or malicious code.
“Security products frequently update their signatures, usually once a day… because they’re always on the lookout for new malware and want to make sure that their customers are safe from the newest threats,” he added.
He said that “CrowdStrike probably didn’t test it as much” because of how often updates are released.
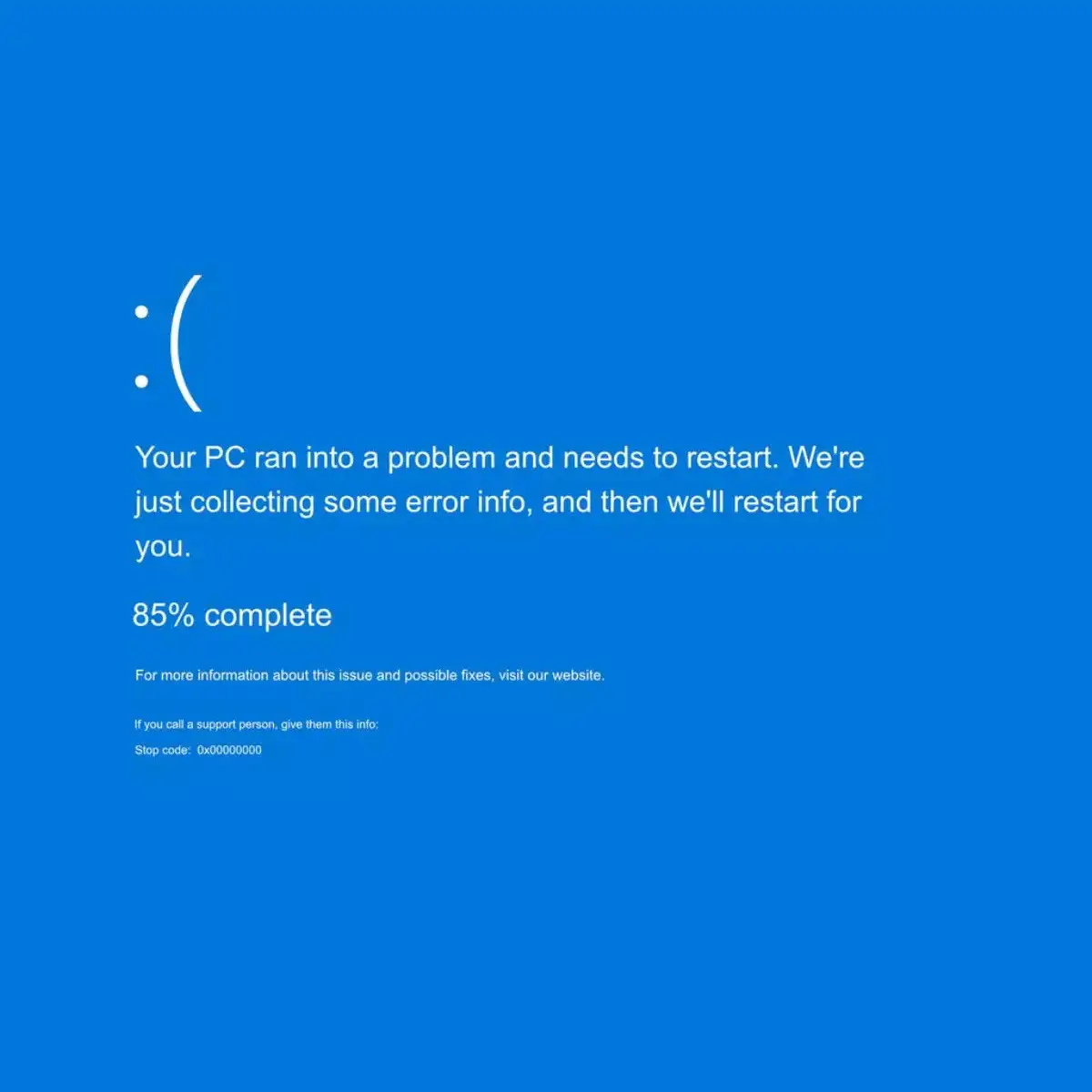
How the flawed code entered the upgrade and why it wasn’t found prior to its public distribution are mysteries.
In an ideal world, this would have been made available to a smaller group of people initially, according to Huntress Labs lead security researcher John Hammond. “That is a safer course of action to prevent a major mess like this.”
There have been similar incidents in the past with other security providers. The 2010 McAfee antivirus update caused hundreds of thousands of machines to halt.
However, this outage’s worldwide effects demonstrate CrowdStrike’s supremacy. The company’s software is used by more than half of Fortune 500 businesses and several governmental organizations, including the Cybersecurity and Infrastructure Security Agency, the leading cybersecurity agency in the United States.